Nowadays, free WiFi at your establishment or event is expected by customers and attendees. How you manage that WiFi experience can mean the difference between a positive or negative encounter for your connected customers or attendees.
MyWiFi Networks enables you to take control of your end user’s WiFi experience through white-label branding, real-time analytics, social authentication, and custom splash pages. Whether you’re looking to promote your coffee shop via social authentication for the WiFi, standardize the WiFi branding at your various retail locations, or provide a professional WiFi experience for your next event, MyWiFi Networks has you covered.
Through integrating with Zapier, you can now connect MyWiFi Networks to over 750+ apps. You’ll be able to capture accounts connected to your social WiFi network as leads in your CRM, automatically add info to shared spreadsheets and marketing campaign tools to easily track users, and stay in touch after a visitor connects to your WiFi. Plus, Zapier is embedded into their intuitive automation feature so you can set up Zaps in seconds.
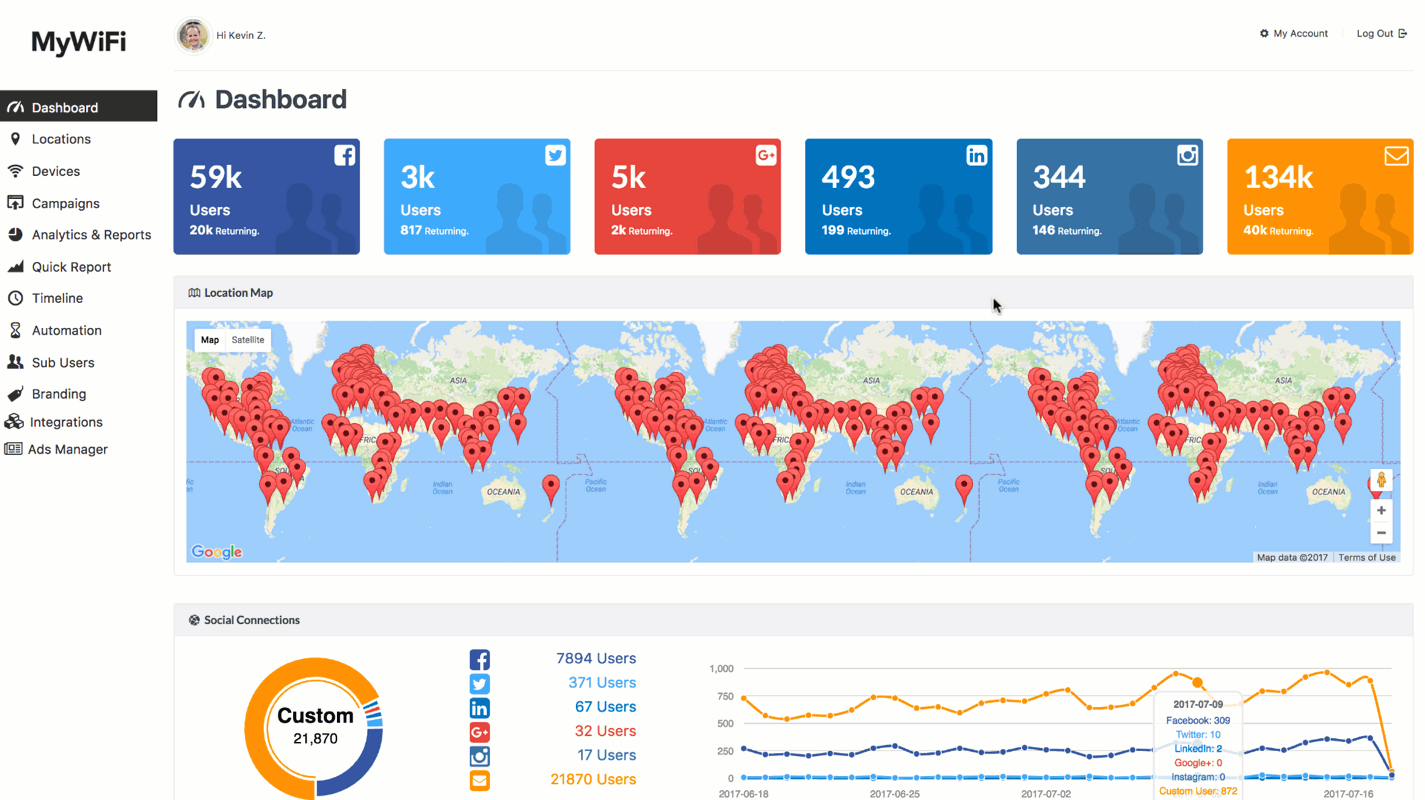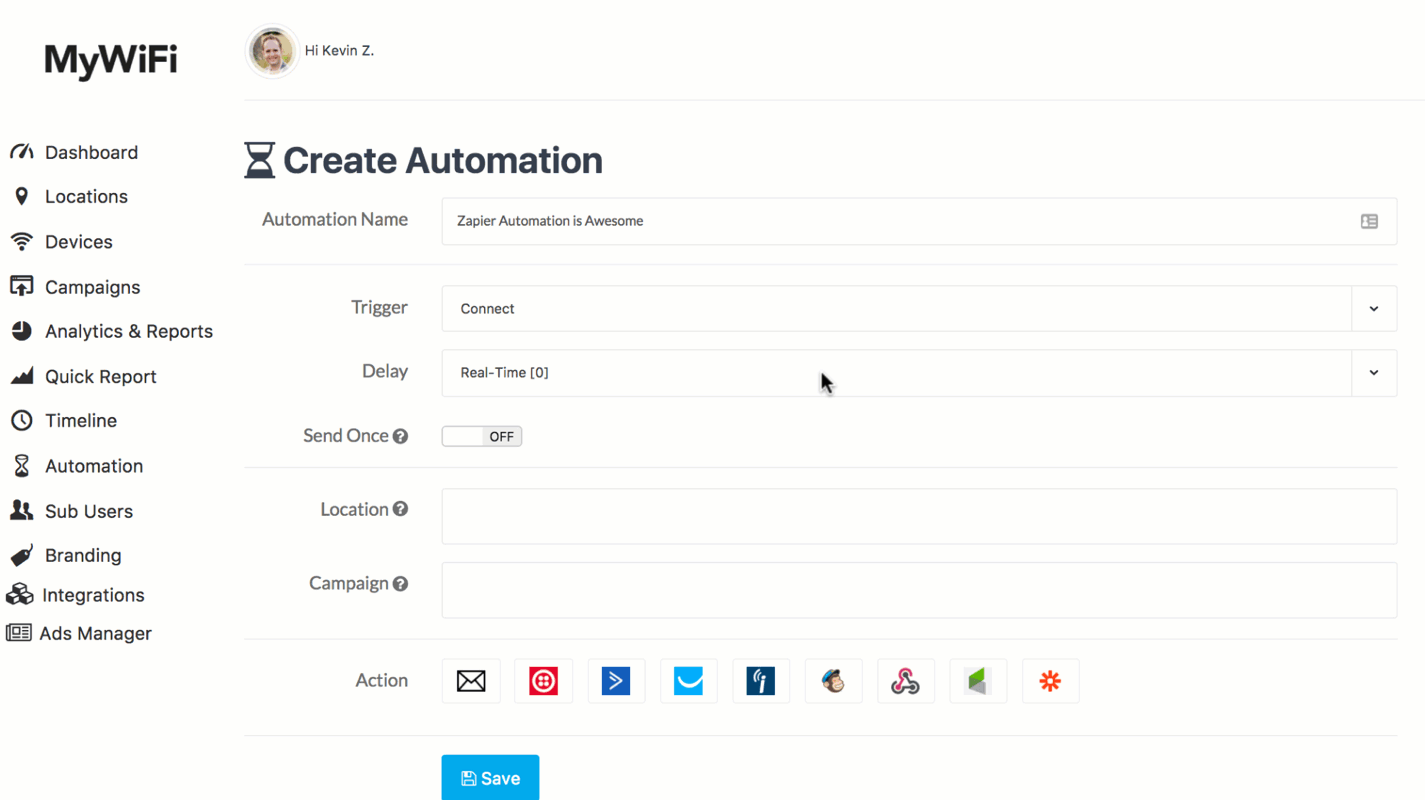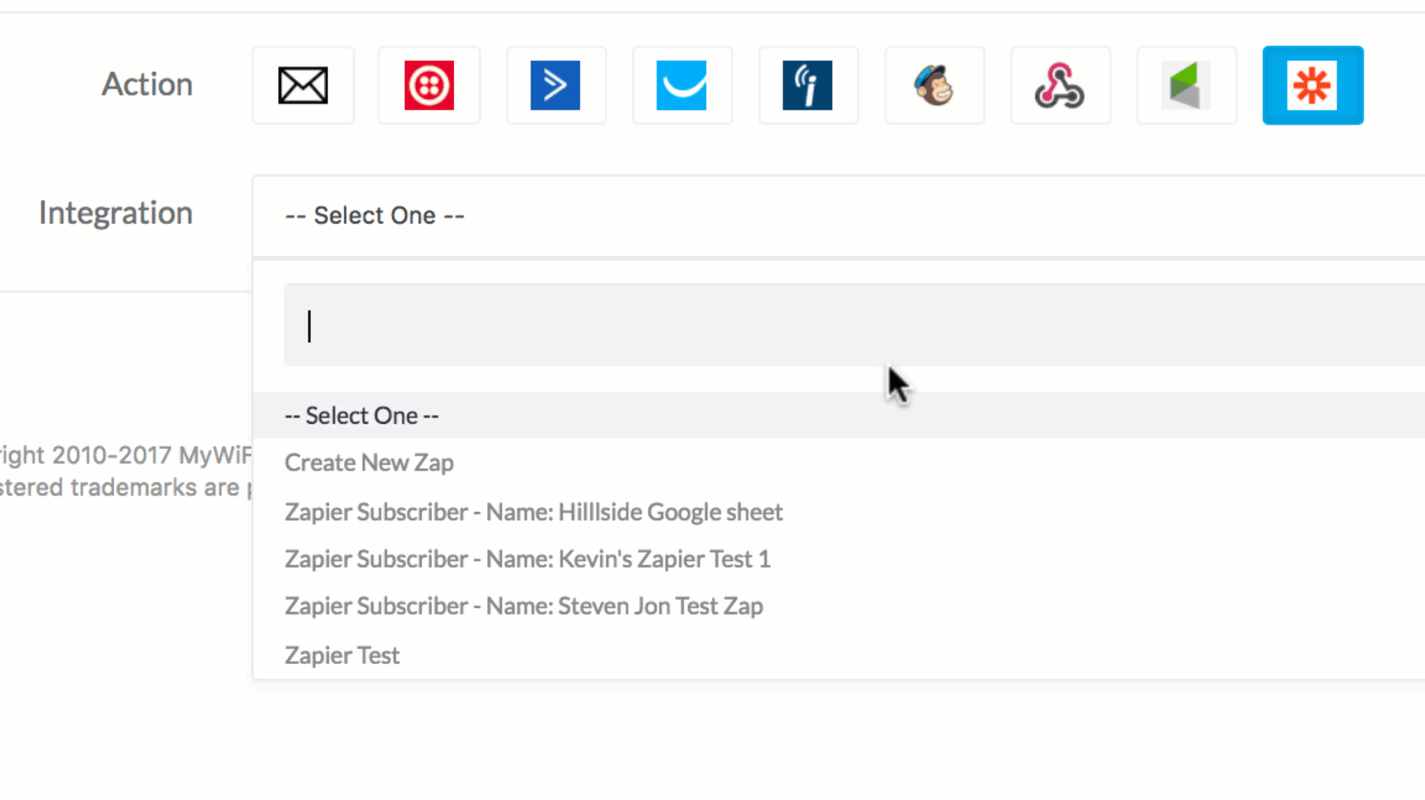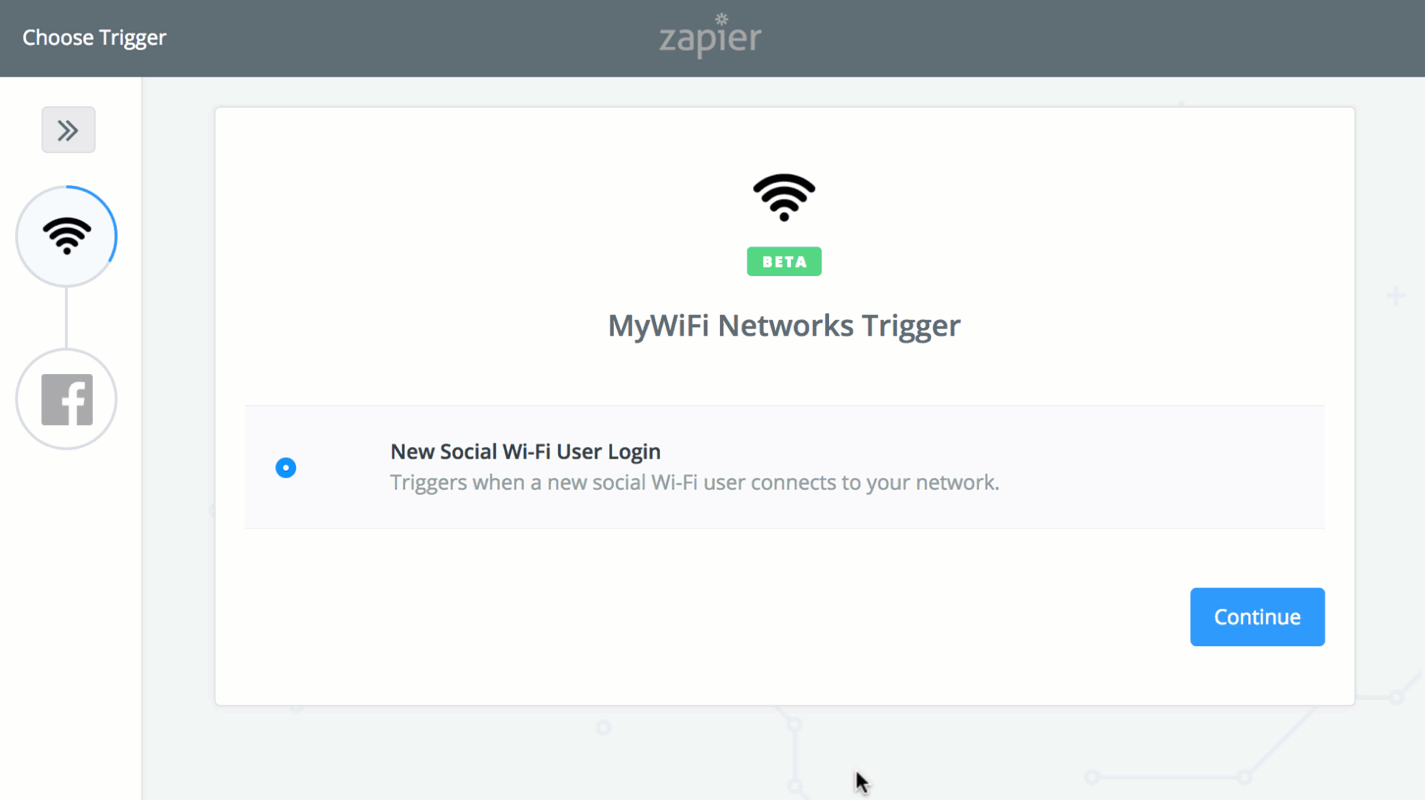
Once you create a Zap, it'll be saved as a template so you can easily apply the same settings for any of the available MyWiFi Networks Triggers. Manage your WiFi offering and improve the user experience with Zapier + MyWiFi Networks.
How MyWiFi Networks Works with Zapier
Triggers
- New Social Wi-Fi Device User: Triggers when a new social Wi-Fi user connects to a device.
- New Social Wi-Fi Campaign User: Triggers when a new social Wi-Fi user connects to a campaign.
- New Social Wi-Fi Location User: Triggers when a new social Wi-Fi user connects to a location.
Automation Inspiration
Get started with these sample Zaps:
Capture Connected Users as Leads in Your CRM
Stay In Touch with Accounts After They’ve Disconnected
How To Automate MyWiFi Networks With Zapier
- Sign up for a MyWiFi Networks account, and make sure you have a Zapier account
- Try some pre-made MyWiFi Networks integrations and learn more about how MyWiFi Networks works with Zapier
- Check out our MyWiFi Networks help documentation for details on connecting your account and setting up your first Zap
- Or login and build a custom workflow with MyWiFi Networks and Zapier





